Directory services
Use the Directory services workspace to configure the connection to a third-party directory service that supports LDAP, such as Microsoft Active Directory or Apache Directory Server for use when configuring user access in the Users and roles workspace (or the Roles screen in SmartSpace Web).
Connecting SmartSpace to a third-party directory service involves:
- Configuring the connection parameters.
- Making sure that the LDAP server interface service is running.
The first time that you search for a user or user group in the Users and roles workspace, SmartSpace will query the third-party directory service and then cache the results:
- Changes to the third-party directory service are automatically detected.
- Cached results for a particular query are deleted if they are not accessed for a given period (for example 24 hours).
- Cached results are cleared if the LDAP server interface service is restarted.
- When you change the way the connection is configured, the service is restarted to connect with the new configuration parameters.
This section assumes you have some knowledge of LDAP or that there is an LDAP administrator who can assist you.
The Directory services workspace
Click on DIRECTORY SERVICES to display the Directory servicesworkspace.
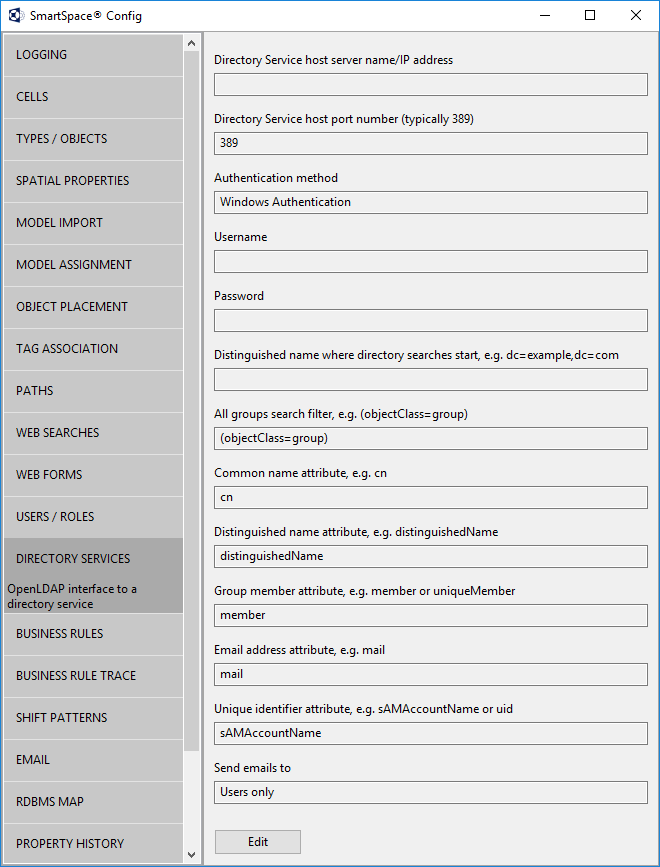
Directory Service host service name/ IP address
The name or IP address of the directory service host, for example the Active Directory server.
Directory Service host port number
The port number on the server which accepts LDAP connections. Typically 389.
To enable secure LDAP (LDAPS) for the connection you must use port 636. By using this port, SSL/TLS is enabled for the connection to the LDAP server (all other port numbers use TCP).
Authentication method
The authentication method used by the server. Either Username and Password or integrated Windows Authentication.
Username, Password
Username and password for server login (if not using Windows Authentication).
Distinguished name where directory searches start
The distinguished name of the root of all searches, for example: dc=example,dc=com
Contact the server administrator for this information.
All groups search filter
The search filter which will return a list of all groups, for example (objectClass=group). This will vary depending on the server.
Common name attribute
The attribute which specifies the common name of a group. When the names of all groups are retrieved, it is this name which is returned. When the members of a group are requested, it is this attribute which is supplied. Typically it is ‘cn’.
Distinguished name attribute
The attribute which is used in the members list of a group. i.e. there will be an attribute of a group which lists all members, this is a comma-separated list containing this attribute for each user. If there is no attribute of the user which matches the names in the members list then choose an attribute which is suffixed with the Root Distinguished Name matching the name in the members list.
Group member attribute
The attribute of a group which contains the list of members, might be ‘member’ or ‘uniqueMember’.
Email address attribute
The attribute of a user which contains their email address.
Unique identifier attribute
The attribute of a user which matches the login name used by the web browser. For example, if the login name is UBISENSE\kevin.white, this attribute should match the bold part.
Send emails to
Whether emails should be sent to users, to groups or to both.
Note that selecting both may result in some users receiving two emails. For example, if there is a group called Support with an email address support@ubisense.net and members Joe and John. If emails to support are forwarded to Joe and John and they both also have email addresses in the directory then selecting ‘both’ will cause emails to be sent to all three addresses and Joe and John will receive two copies.
The common name of a group (as displayed by SmartSpace) might differ from the name seen in a mail client if there is a displayName which is different.
Configuring LDAP
- Open the Directory services workspace.
- Click Edit to configure LDAP settings for your SmartSpace installation.
- Click Save when you have finished entering the details.
LDAPS on Linux
Getting LDAPS to work can be difficult on a Linux platform server. If the server is a member of a Windows domain, then usually the required certificates and configuration will already be set up. But for accessing a non-windows LDAP server using LDAPS, diagnosing problems can be difficult.
The Ubisense LDAP integration uses the OpenLDAP libraries on Linux. Ensure that the OpenLDAP client configuration has been set up correctly on the server. Typically the configuration will be in /etc/openldap/ldap.conf, and the root CA used to sign the LDAPS server certificate should be placed in /etc/openldap/cacerts. The ldap.conf should be set to try to verify the certificate:
TLS_CACERTDIR /etc/openldap/cacerts TLS_REQCERT demand
To check that this is working, use the ldapsearch command-line tool:
ldapsearch -H ldaps://ldapserver.my.domain -x -b "dc=example,dc=com" -s sub "(objectclass=group)"
Here the filter supplied at the end of the command line should match that entered in the All groups search filter. If this returns a list of group names, then the OpenLDAP client configuration is working. If not, you can see extensive debug information by using the verbose flag “-v”, or if still unclear, full debug level “-d 999”.
If there is a problem with the LDAP server certificate, then it is possible to turn off certificate checking in the client configuration, though this is not recommended for a secure production deployment. To turn off certificate checking at the client for testing, set the following in ldap.conf:
TLS_REQCERT never
To see extra information about LDAP processing in the Ubisense platform, enable the “ldap” platform monitor stream, and restart the “Visibility/LDAP server inferface” service. The logs will now show ldap queries executed, and what they returned.
If connecting to an OpenLDAP server that requires a user and password, it may be necessary to provide the full distinguished name of the user in the “username” field.